TLS deciphering improvements
First release of TLS deciphering was 1 month ago, and many improvements have been done after these few weeks of run.
- Observability of discovery phase has been enhanced and fixed to help understanding what is captured
- TLS 1.2 deciphering has been added
- Many UI and deciphering fixes
Observability enhancements
Now, on top of showing the OpenSSL libraries on which the probes are attached, Spider is showing them together with the processes / the applications using them. With their deployments.
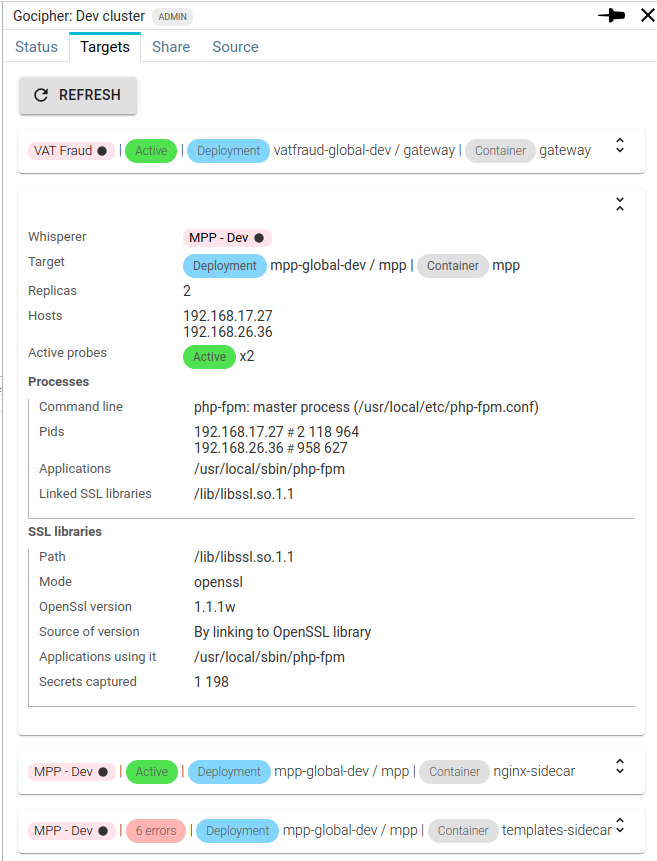
It helps understanding why a probe may not have been attached. Such as when the container is running sleep command...
There is no OpenSSL library linked to sleep ;)
Spider then tries to find a default one:
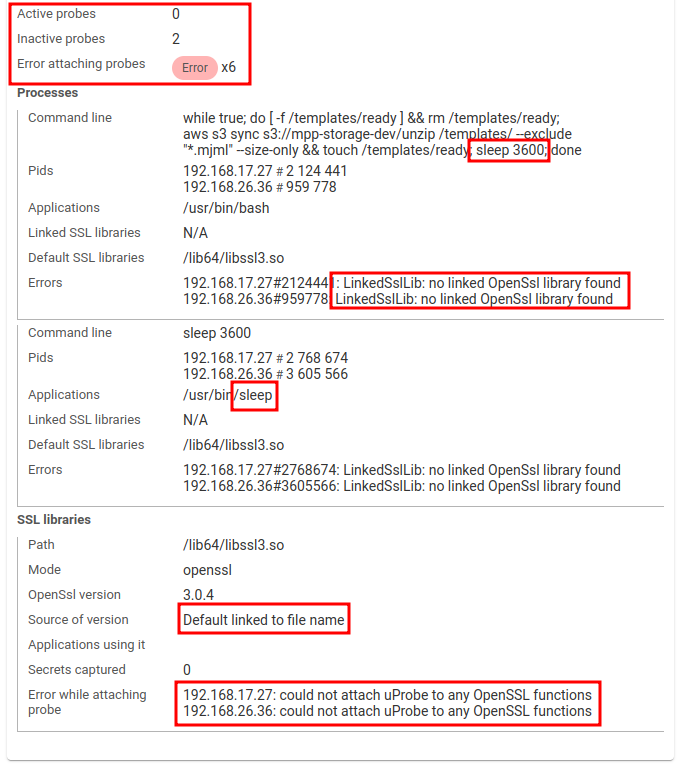
In the screenshot above,
- Spider found bash and sleep processes on 2 replicas
- These are not linked to OpenSSL libraries
- So Spider looked for and has found a default one in
/lib64 - But Spider could not attach to any OpenSSL function... because it may not be OpenSSL at all - the image was
aws-cli.
TLS information in TCP sessions
TLs encryption information has been added in TCP Global tab and TCP grid:
- Tls version
- Cipher name
TLS 1.2 deciphering
Previous version was limited to TLS 1.3.
Now, Spider does decipher TLS 1.2 protocol! :)
It was though, with the various ciphering modes and processes. Plus the fact that extensions as Encrypt-Then-Mac change the process for the same Cipher.
The list of supported libraries, protocols and ciphers are available in TLS sessions documentation.
Bug fixes
Also, some bugs were fixed:
- on some cases the Gocipher was spawning several probes on the same library.
- for some TLS servers such as AWS services, the handshake was cut short, and Spider could get the secrets only too late. I found a way.