Decoding CN from X509 certificates
Spider now extracts identification from X509 certificates while parsing.
Story
I finished my first round of development for Floocus and its license / invoicing system. It is up and running now :)
So... back to Spider! And I have a few value added task to do for you guys!
When moving Streetsmart to the Kube, Spider was moved as well (of course). And Spider sees more stuff on the Kube than on Swarm!
One of them was that we capture (for now) all queries to the gateway (as well as from the gateway). When calling the gateway, machines clients are calling using their own certificates as authentication, which is transmitted in x-ssl-cert HTTP header for Keycloak auth.
Example of a transmitted certificate, as seen with SSL cert decode plugin:
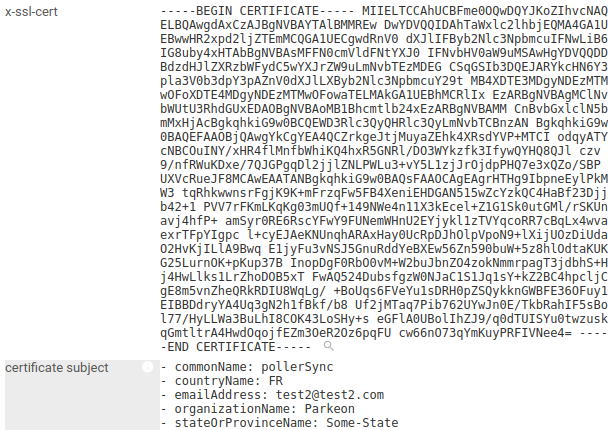
Fine. But this one is not taken into account in 'identification' field that is much useful to filter coms.
That's fixed! :)
Now Spider decodes the PEM in the header to extract and store the identification and allow filtering in those.
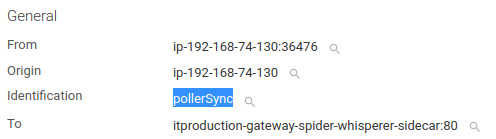
And as soon as certificate auth will be moved to native mode with Keycloak, extracted identification value will be the same for JWT AND Certificates! Which will simplify much the follow up :)
Code
Honestly? I'm ashamed: 4 lines of codes added to the parser... I should have done it before!