Secure shared secrets for local dev using Vals
Spider now uses Google Sheet to store and manage access secrets used in local dev!
Sounds crazy? Read further!
Context
Spider needs a single values.yaml file for its whole setup using Spider Helm chart.
However, this leads to having a file in the repository with all secrets and credentials necessary to run the system, written in clear form, and potentially accessible to all.
How to avoid this?
Solution
The community has come up with a nice tool to deal with this situation: Vals.
Vals allows to store pointers to secrets in your values.yaml, having these secrets stored in a secret manager such as Hashicorp Vault, AWS SSM, AWS or GCP Secrets managers...
We use is at my daily work to secure credentials for production and other Kube environments.
The DevOps team did a great job finding this out and configuring Argo CD with it.
Vals also has a weird back end: Google Sheet?
Why?
I don't know what the authors had in mind, but I found the idea really great!
When developing locally, you might not have access / or need / to AWS or GCP account, you might not have a shared and accessible Vault... so how can you share something completely secure, with access rights management, accessible to all, and easy to access?
Google Sheet is a very nice solution for this! And Google APIs allow it in a couple of lines. 😁
So I did implement it on my local dev.
How does it work?
- Create a Google Sheet to store your credentials as a simple table in the first (and maybe only) sheet as [Key | Value]
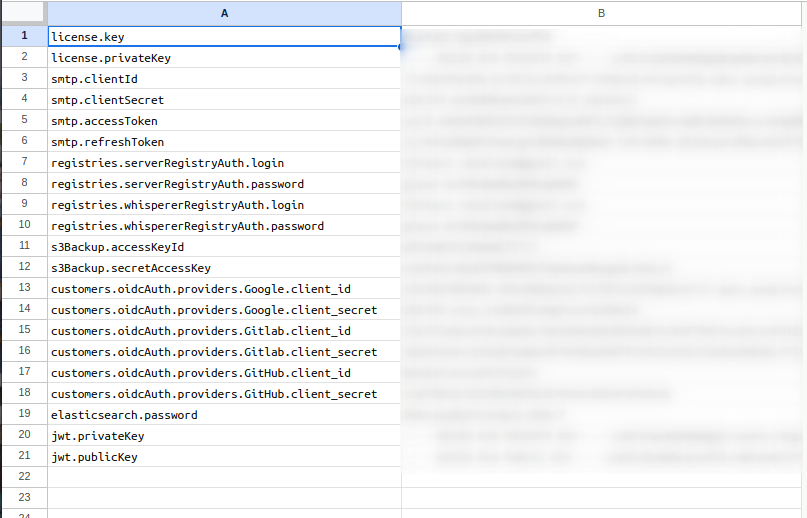
- Replace your credentials in your
values.yamlfile with Vals Google sheet URIs schemes
global:
version: latest
endpoint:
host: spider.localhost
publicPath: http://spider.localhost
license:
key: ref+googlesheets://ABDEFEF_hijklmnop?credentials_file=../credentials.json#/license.key
privateKey: ref+googlesheets://ABDEFEF_hijklmnop?credentials_file=../credentials.json#/license.privateKey
jwt:
privateKey: ref+googlesheets://ABDEFEF_hijklmnop?credentials_file=../credentials.json#/jwt.privateKey
publicKey: ref+googlesheets://ABDEFEF_hijklmnop?credentials_file=../credentials.json#/jwt.publicKey
- When generating the manifests for Kube, Helm+Vals converts external secrets reference to their value before sending to Kube
How to
- Prepare your
Google Sheetandvalues.yamlfile as shown above- Extract the
spreadsheetIdfrom the Sheet URL, as in https://docs.google.com/spreadsheets/d/{spreadsheetId}/edit#gid=0
- Extract the
- Install Helm secrets with:
helm plugin install https://github.com/jkroepke/helm-secrets - Get a service account following Google help
- Save this service account json key into a
credentials.jsonfile relative/absolute to your repo - Your service account email must have the read permission to your Google sheet storing Credentials
- Download Vals binary from
https://github.com/helmfile/vals/releases/and copy it in your PATH (for example/usr/local/bin) - Last part, when using Helm, use
helm secrets <command>instead of plainhelm <command>:helm secrets -b vals upgrade spider -f values.yaml spider-analyzer --namespace spider-system --create-namespace --install
And that's all! Your secrets are now manage easily and may be securely shared with all developers :)
It is so weird but effective that I felt like sharing it !
Cheers,
Thibaut