Installing Spider Gocipher
A Gocipher is installed automatically in the Cluster where Spider is setup.
But you may install it as standalone in any other cluster!
You have two ways to install the Gocipher in Kubernetes.
- An easy, one line installation. That may be used for testing.
- A more 'standard' one, using a configuration file.
Both installations are described and use the Installation tab of the Gocipher details:
You may also install and use a Gocipher outside Kubernetes, as a standalone, by using directly its executable.
You cannot delete or reinstall the local-controller setup in Spider own cluster.
UI
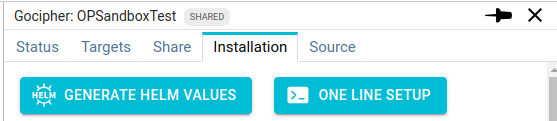
Clicking on any of the buttons regenerate the API key of the Gocipher, invalidating the previous one.
One Line
When clicking on the ONE LINE SETUP button, a command line is copied in your clipboard.
Pasting it in a shell configured to execute Helm on your Kubernetes cluster will install a Gocipher
with default settings.
Example of generated command:
helm upgrade spider-gocipher \
--repo https://repository.floocus.com/helm/ spider-gocipher \
--set gocipher=JfavkPIBTTekbSJdE5SHQQ \
--set privateKey='-----BEGIN RSA PRIVATE KEY-----\\nMIICXAIB...ItcRSuoAIpol4R9tWZbzaA6kk=\\n-----END RSA PRIVATE KEY-----' \
--set spiderConfigURI=http://spider.hub.company.com/ciphers/v1/gociphers/JfavkPIBTTekbSJdE5SHQQ/config?view=client \
--namespace spider-controller \
--create-namespace \
--install
The Gocipher needs to be setup in the Controller namespace as it communicates with it directly with its service name.
Helm values.yaml file
Clicking on the other button GENERATE HELM VALUES, Spider generates the base of the values.yaml file required to use Helm:
---
gocipher: JfavkPIBTTekbSJdE5SHQQ
privatePem: '-----BEGIN RSA PRIVATE KEY-----\nMIICXQIBAAKBgQCfXBWrzSLC6kF...BDD55pKw56q\n-----END RSA PRIVATE KEY-----'
spiderConfigURI: http://spider.hub.company.com/ciphers/v1/gociphers/JfavkPIBTTekbSJdE5SHQQ/config?view=client
To use it, first, you need to register Floocus Helm repository:
$ helm repo add floocus https://repository.floocus.com/helm
You may check latest versions available with:
$ helm search repo floocus
Then, use the values.yaml file to install:
helm upgrade spider-gocipher floocus/spider-gocipher \
-f ./values.yaml \
--namespace spider-controller \
--create-namespace \
--install
That's all!
The Gocipher connects to Spider, and it will be used to capture TLS secrets 😀.
Customisation
Version
gocipher:
image:
tag: 2024-10-15
You may define the Gocipher version. The version is linked to the system version of Spider.
Others
You may check the available values in values.yaml file for extra 'standard' configuration options.
- hostAliases
- affinity
- toleration
- ...
$ helm show values floocus/spider-gocipher
Gocipher standalone deployment
This deployment is meant 'standalone' as it is running outside Kubernetes. But the Gocipher still works only when connecting to Spider server.
Download
You may download the Gocipher executable on official Floocus repository:
https://repository.floocus.com/bin/gocipher-x86_64/1.0.0/gocipher.xz
The changelog gives links to the latest releases associated with their SHA-256 hash to check that you have the official package.
Content
Gocipher comes with few siblings in its .xz package. These executable are used to extract OpenSSL version of the targes.
| Binary | Description |
|---|---|
gocipher | Gocipher main binary |
nsExe-libc | Used to call node.js in the container own namespace to get its OpenSSL version. Libc version. |
nsExe-musl | Same as above for Alpine containers. |
ossl_version-libc | Used to bind to libssl.so of the container to get OpenSSL version. Libc version. |
ossl_version-musl | Same as above for Alpine containers. |
Configuration
Gocipher requires 2 configuration files, in current working directory, to run as standalone:
config.jsonholding the same configuration as the values, in JSON:
{
"gocipher": "H5ZyP60dTt6ySEVgXW69Dw",
"spiderConfigURI": "http://spider.hub.company.com/ciphers/v1/gociphers/H5ZyP60dTt6ySEVgXW69Dw/config?view=client",
"privatePem": "-----BEGIN RSA PRIVATE KEY-----\nMIICWwIBAAKBgQCOD...g50lQMe3b5Z/AQ==\n-----END RSA PRIVATE KEY-----"
}
toWatch.jsonholding a list of targets to watch
[
{
"whisperer": "oWl09MaiTVOz6Kuk7H9eOg",
"target": "containerd://1671fd1f5865becf6b4fa63c684b149711279ea897bb3db086d166abb889cede"
}
]
Targets to watch are a couple: whisperer + target.
whispereris the id of the whisperer capturing the network on the same host, and for which we want the TLS keys,targetis the... target
Target are URIs like that identify the executable / OpenSSL library that you want to watch.
Options are:
| URI | Description |
|---|---|
containerd://{id} | Target is a container running with containerd. Gocipher will look for it in /proc, find all running processes, and hook inside their OpenSSL library. |
docker://{id} | Same as above, with docker runtime. |
pid://{number} | Target is a running process. Gocipher will look for it in /proc, find all running processes, and hook inside their OpenSSL library. Gocipher will only capture secrets from this PID. |
file://{pathToExecutable}file://{pathToLibSsl.so} | Target is an executable or OpenSsl library. Gocipher will open it and hook inside. Gocipher will capture all secrets... |
When used withing Kubernetes, Gociphers are asking targets to Controllers, that send a list of containerd or docker
targets, together with metadata describing the container: namespace, pod, parents.
Run
To run Gocipher as standalone, unzip the package, and launch it as any other program.
./gocipher