Network Packets
Concept
Packets are captured one-by-one by whisperers.
Visualisation tools and searches capabilities around packets are for now quite limited.
In fact, once correctly configured, you often never look at packets and it is even a best practice not to save them at all!
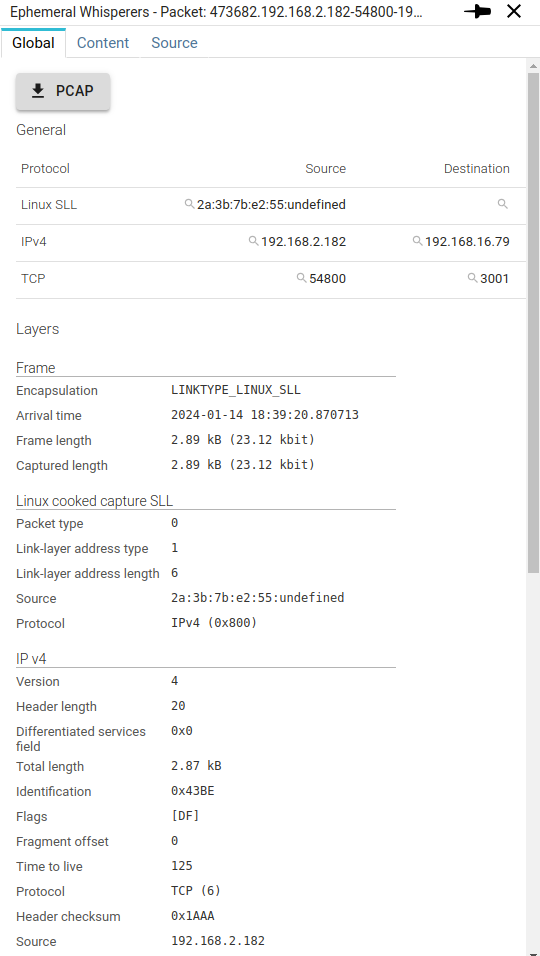
Global tab
Packets are stored in raw format, but decoded for display on the UI Only metadata is searchable.
Each icon in the details shows a prebuilt filter.
Clicking on it adds a filter in the selected filter.
General
Shows all source and destination 'identifiers' of the packet in its different layers.
Layers
Protocol layers are decoded on the UI to display internal packet data.
Layers fold in and out to display data
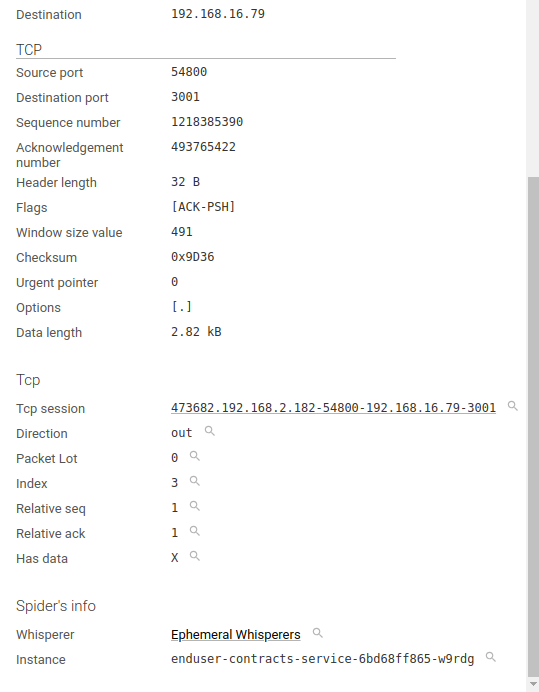
Tcp session metadata
This shows the Tcp metadata Spider attached to the packet to allow streaming decoding.
| Field | Description |
|---|---|
| Tcp session | Link to the Tcp session details |
| Direction | in/out |
| PacketLot | Number of the packetLot (group of packets with data in the same direction) |
| Index | Index of the packet in the Tcp session, since its start |
| Relative Seq | Relative SEQ number from session start |
| Relative Ack | Relative ACK number from session start |
| Has data | Tells if packet has Tcp payload (used for parsing) |
Spider information
| Field | Description |
|---|---|
| Whisperer | Link to the Whisperer |
| Instance | Instance of the Whisperer that captured the packet |
Actions
You may export the network packet in a .pcap file by clicking on PCAP button.
The pcap file may then be opened in many tools like Wireshark.
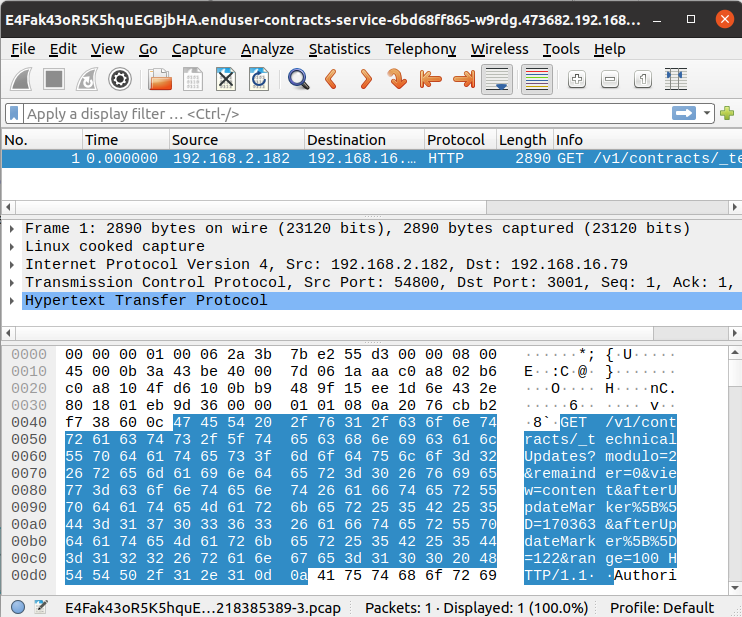
It may even be uploaded back to Spider 😉
Content tab
Decoder
The content tab gives access to the packet content.
You may choose the decoder to use for display.
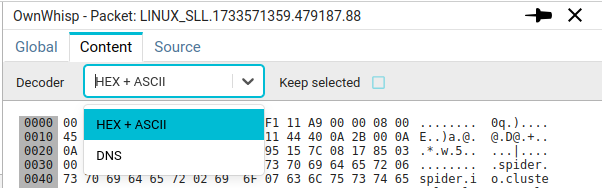
When Keep selected is checked, your selection is kept for all subsequent packets you may open.
HEX + ASCII mode
This mode shows the raw packet as transmitted over the network.
The representation is classic:
The left part:
- shows the data in hexadecimal
- grouped in words of 16 bytes and lines of 32 bytes
The right part shows the ASCII version of the same data, to help read the text that may be inside.
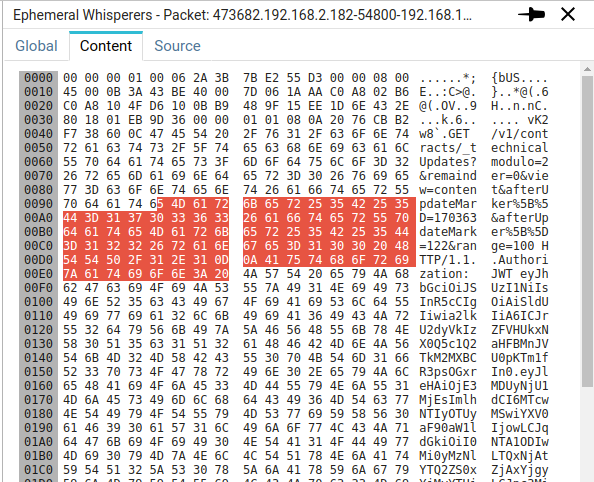
You may copy the hexadecimal part or the textual part independently and without the extra spaces used for representation.
Nice; isn't it? 😉
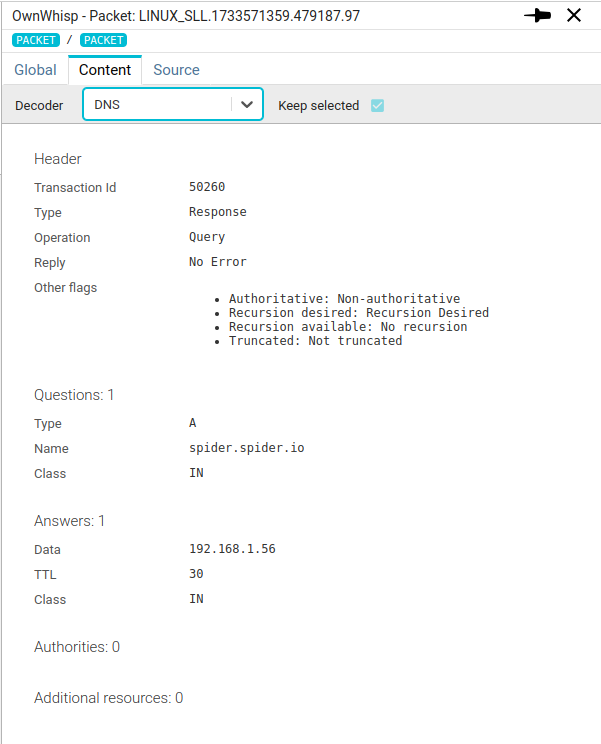
DNS decoder
DNS decoder tries to parse the network packet as a DNS packet and displays its content.
Source tab
The Source tab shows the packet in JSON format.
Below is a sample packet as it is available through the API:
{
"@type": "Packet",
"version": "2.0",
"whisperer": "E4Fak43oR5K5hquEGBjbHA",
"instanceId": "enduser-contracts-service-6bd68ff865-w9rdg",
"@id": "E4Fak43oR5K5hquEGBjbHA.enduser-contracts-service-6bd68ff865-w9rdg.473682.192.168.2.182-54800-192.168.16.79-3001.1218385389-3",
"commonId": "E4Fak43oR5K5hquEGBjbHA.473682.192.168.2.182-54800-192.168.16.79-3001.1218385389-3",
"name": "473682.192.168.2.182-54800-192.168.16.79-3001#3",
"tcpSession": "E4Fak43oR5K5hquEGBjbHA.enduser-contracts-service-6bd68ff865-w9rdg.473682.192.168.2.182-54800-192.168.16.79-3001.1218385389",
"timestamp": 1705253960.870713,
"date": "2024-01-14T17:39:20.870Z",
"dateCreated": "2024-01-14T17:39:22.780Z",
"minute": "2024-01-14T17:39:00.000Z",
"protocolsList": [
"Linux SLL",
"IPv4",
"TCP"
],
"length": 2890,
"rawPacket": {
"link_type": "LINKTYPE_LINUX_SLL",
"buf": {
"type": "Buffer",
"data": [0,0,0,1,0]
},
"header": {
"type": "Buffer",
"data": [72,28,164]
}
},
"protocols": {
"Linux SLL": {
"src": "2a:3b:7b:e2:55:undefined",
"dst": null
},
"IPv4": {
"src": "192.168.2.182",
"dst": "192.168.16.79"
},
"TCP": {
"src": "54800",
"dst": "3001",
"direction": "out",
"packetLot": 0,
"index": 3,
"relativeSeq": 1,
"relativeAck": 1,
"hasData": true,
"plTooBig": false
}
}
}
Most fields are self-explanatory. Most fields are indexed and searchable, except the buffers.
Some extra explanation:
| Field | Description |
|---|---|
| @id | Unique id of the packet |
| commonId | Used when avoid duplicates is active. The instanceId is not embedded. |
| dateCreated | Date when the packet was registered in the backend |
| plTooBig | Not taken into account in parsing as the packetLot was too big |
When a packet arrives too late (often due to network issues), the packet is marked with packetLot: -2.